The gadget and you are on vacation. How to use the Internet safely when traveling
The ease with which people can steal your personal information is the cost of banking, shopping and communicating online. To use the Internet safely, use the following strategies.
Method 1: Protect your personal information
1. Don't use simple passwords. Using the word “password” or the set of numbers “1234” as a password is like putting a house key in front of the entrance. Fraudsters can easily guess and crack the password. Instead, create a long password that contains both letters and numbers (signs). It is advisable that the password relates to something important to you. For example, if you had a pet goldfish as a child and his name was Mr. Bubble, you might come up with a very good and complex password, such as “mr1pozyr736,” that only you can understand. Write down all your passwords.
2. When subscribing to the mailing list, downloading files, signing agreements, always read the fine print. If you do not want to receive junk mail or be put on telephone agent lists, please note the small box at the bottom of the page that asks if you want to receive information and offers from other companies.
The best sites themselves state that they will not sell your data to other companies (although they themselves may send you a lot of junk mail). Some sites require you to provide all your information in order to receive their product. Fill in only required fields marked *. If the information field does not have an asterisk, then filling it out is optional and you can leave it blank.
3. Do not give your full name, address or telephone number to anyone online unless you trust and know the person personally. This is especially important in chat rooms or when negotiating for work or on sites designed to meet or find people with common interests. Beware of letters that give very vague answers and there is no clear answer to any of the questions you asked, as well as letters that talk about non-cash payment or the conclusion of any business agreement while the representative is “abroad”, or o receiving gifts or inheritance from an unknown source.

4. Be careful and don’t fall for online scams. Beware of fraudulent emails claiming to be from eBay, PayPal, a bank or a company you trust. These emails request personal or confidential information. This is called phishing. This email may notify you that there is a problem with your account or password. The email may contain a link that you need to click on.
Forward any of these letters to the name of the company on behalf of which it claims to have been sent. They will confirm whether the email message you received was real or not. Also, keep in mind that some email services such as Yahoo!, MSN, Hotmail. Gmai, Mail.ru never specify your email password. Don't fall for scammers.
Method 2: Protect your data and connections

1. Make sure that you use (and regularly update) anti-virus, anti-Shionware programs and a firewall. You can use, at your discretion, either an access restriction system (firewall) purchased with your operating system or a program purchased from other suppliers. Do not use the two systems together as they may interfere with each other.

2. When you use a public wireless connection, turn off file sharing and network discovery features. Both of these features put your files, messaging, and system at risk of being opened by anyone over the air, not just hackers. On Windows, these features can be disabled via Control Panel > Network and Internet > Network and Sharing Center. On Macintosh, features can be disabled through System Preferences > Sharing.
If there are many wireless sources around you but you do not need to use the Internet, turn off all your wireless devices. On some devices this is just an on/off switch, on some devices you will need to configure this yourself, for example on a Macintosh you need to click on the Wi-Fi icon and turn off AirPort.

3. Always verify information about secure transactions. The best companies have many safety features. You can see a golden padlock at the bottom of the page which indicates the site is secure. When you provide any bank details or other information, please ensure that the connection is secure (the URL should start with "https://" instead of "http://") and that the site is trustworthy. Not every site that runs HTTPS or accepts payments is trustworthy, even if it has the required secure connection.

4. Set your browser to block inappropriate information, especially if you have children.
1. Download files or software from sites that have been rated or verified by reliable sources. Use download resources that have high ratings and verified prices, and that carefully review the files they provide for download (for example, download.cnet.com). If you doubt the security of a site, then either simply search the name of the site in search engines, or search along with the word “scam” to see if the search engine returns any results. Do not illegally download copyrighted products without paying for them.

2. Never open attachments in email received from unknown recipients, unless you trust them and you have security settings on your computer. Some unwanted emails may contain viruses or spyware that can harm your computer. Such emails may be automatically marked as "spam" or "junk", but virus-infected emails from unsuspecting friends can also slip into your inbox.
- If you use email programs such as Outlook or Thunderbird, then disable the attachment preview feature. Since with this function you cannot decide for yourself whether to open the attached file or not. Look in the settings of your email program and disable options such as “Show Attachment Previews”, “Display Attachments Inline"s” and so on.
Adviсe
- It is best to have three email accounts. One for friends and websites, another only for work issues, the third for personal clients, banking correspondence, job searches and other things that require increased protection. Use a suitable name and a strong password for your last two email addresses. Some companies may keep your work email address after you leave, so make sure you have a backup copy of all the documents you need.
Warnings
- Keep a backup of important emails and documents on a flash drive, in hard copy, or both.
- Use good test questions that only you know the answers to.
- Abandon your email or any accounts that have been hacked after you have copied any data that can be saved. Immediately notify your bank or workplace about such changes. You may have to change all passwords or account numbers and similar information immediately (if it was ever mentioned in your email). Complain about the problem directly to the representative of the organization providing your email services.
- If your computer is hacked via the Internet, then all your information may be at risk. Update your virus protection and remove the virus. If important documents or information have been stolen, notify your bank and place of business. Report the crime to law enforcement.
Five tips for virtual travel without fear.
Don't connect without knowing the risks.
Whether it's a local bar, a city-owned network, or a hotspot from your mobile operator, public Wi-Fi networks continue to proliferate. Especially in business districts, where you will instantly find a high-speed network to connect to.
However, network access is usually granted with the requirement of some personal information. Once connected, you find yourself sharing the network with many other people - and some of them may be willing to spy on your activities.
Below are five tips for using public Wi-Fi safely while protecting your information.
1. Consider the risks
Don't stay online longer than you have to.
Public Wi-Fi is inherently less secure than your home network because you're sharing the network with dozens, sometimes thousands of strangers, rather than a small group of people you trust. So if you want absolute, 100% privacy and security from public Wi-Fi, just don't use it. And if you absolutely need to make this contact, then keep in mind that you are taking on the risk that a complete stranger can spy on your Internet session.
How will this knowledge help you? With this in mind, using common sense and caution, you will ensure that the session does not become dangerous. If possible, avoid making bank transactions or viewing business emails. Choose neutral activities - browsing sports or news sites or something similar where it doesn't matter whether your actions are being observed.
In addition to being careful in the actions themselves, try to follow these rules: stay online as little as possible, disconnect the connection immediately after you finish, and make sure that the anti-virus software on your laptop and phone remains up to date.

2. Read the fine print
Don't ignore security policy pop-ups.
We all believe that we need to read the fine print, but we don't actually follow that advice. This is especially important when connecting to a public Wi-Fi network. What exactly do you provide instead of wireless Internet? How is your email, phone number, or anything else going to be used?
You are essentially putting your trust in the company or individual not to spy on you. Take a popular chain of coffee shops: the brand is unlikely to covertly monitor customers' online activity, but rather collect insignificant information for marketing purposes. Therefore, weigh the options and make a choice.
For completeness, you can read the Wi-Fi access rules set by the brand in advance. Before going out into the city, if you know your future route, you can identify establishments where it seems safer to connect.

3. Opt for an HTTPS connection
The green “HTTPS” beginning in the link text indicates increased connection security.
When your browser navigates to a site whose URL begins with “https://,” a green padlock icon appears in the address bar. This means you're on a site that uses Hyper Text Transfer Protocol Secure, or HTTPS, jargon for using an encrypted connection to that site.
In fact, HTTPS mechanisms encrypt all of your activity on a given site. This makes it difficult for someone sitting behind you in a cafe, or the owner of a hotel router, to track the data you share. If possible, only visit sites that use this protocol.
As we said above, it is better to visit sites with general information when using public Wi-Fi, rather than browsing through social networks or email.
However, if you need to visit a site with more sensitive information, pay attention to the green padlock and “HTTPS” to ensure security. Luckily, most popular sites that require authentication, from Google to Facebook (and Orbios among them), now use HTTPS.

4. Install a VPN
Choose a VPN, but choose wisely.
Installing a VPN (Virtual Private Network) application is perhaps the most effective way to safely use public Wi-Fi, accessible to everyone. But even this does not provide a complete guarantee of safety. While providing the ability to spoof your location or watch foreign TV, a VPN also encrypts all data sent and received through your computer or phone. Like working with HTTPS, the program will make it much more difficult for other people on the same network to spy on what you're doing.
You'll have to spend some time choosing a quality VPN because, essentially, you'll be entrusting all your Internet traffic to its developers. As a rule, reliable and fast work implies payment. If you intend to use a reliable and proven service, pay attention to this regularly updated rating of VPN applications. We wrote in more detail about VPN.

5. Select a network
Not all Wi-Fi networks are configured the same.
The operating principles of different Wi-Fi networks are not the same. Since there are usually several networks to choose from to connect to, you should make the best choice. Any network that has a complicated connection to it, such as buying a coffee, asking the staff, or paying a small fee, will be significantly more secure than a completely open network that anyone can use.
For security reasons, you should also choose a network created by a well-known company or brand, and avoid networks that appear out of nowhere. Finally, we recommend that you still connect to the same networks at the same establishments. The more access points you use, the more companies you give away your personal data to be torn to pieces.
Orbios uses all technologies that increase the security of your session, but you should not neglect the described rules when working with any sites.
Everyone knows from childhood that electrical appliances require special attention, but annoying troubles involving them arise with enviable regularity. Expert advice based on an analysis of the causes of fires and injuries due to the incorrect use of electrical appliances will warn you against such troubles.
1. Under no circumstances should you use any electric heating devices that are made using the “handicraft” method for heating.
2. The devices should not have any damage or malfunctions that could lead to fires, for example, damaged insulation, faulty thermostats, unstable stands.

3. Do not leave electric heating devices plugged in unattended. This will not only save electricity. Note that the main role of a device such as a thermostat is to turn the heating device off and on. In general, the temperature controller allows you to solve a lot of different problems. It is especially convenient to use it in apartments where they use the “Warm Floor” system.

4. Do not use any electric heating devices to dry clothes or linen.

5. When using an iron, electric stove, electric kettle, electric fireplace, you need to install them at a distance of at least 0.5 meters from flammable objects.

6. It is imperative to constantly monitor the serviceability of electrical wiring, the condition of insulation and the integrity of all electrical products in the house. If there is any doubt that you can install the wiring correctly or repair the damage, contact an electrician. Saving can be costly.
The magical time of the New Year holidays is approaching, which means it’s time to travel.
The modern user wants to be in touch everywhere and 24 hours a day. Traveling is not a reason to give up constant communication. Just the opposite. When traveling, users are increasingly using their gadgets in a variety of situations - from searching for information about attractions to paying for air tickets. But what dangers could lie in wait for them? And how to protect tourists active on the Internet and their gadgets while traveling? AiF.ru asked Kaspersky Lab specialists about this.
Internet on the go. Is it safe?
According to statistics, many literally do not let go of their gadgets - smartphones, tablets, laptops. Moreover, they do not part with them even when traveling - after all, with their help you can publish photos on social networks, check in, write statuses and keep abreast of all events. 50% of users actively use the Internet in public transport, 44% connect it in their car, 70% press buttons right in bed, as soon as they wake up.
If we take into account the fact that many of them store important confidential information on their personal devices, the loss of which can lead to significant financial troubles, then we can understand why such users are of great interest to hackers.
Paradoxically, few users, when storing important data on their devices, think about their security. Despite the fact that hackers can easily intercept data and passwords, only 27% limit their activity and only perform secure actions when using open networks. These are the statistics from Kaspersky Lab.
Most users are not so vigilant - for example, 17% register on websites and log into their accounts, and 4% even make purchases or banking transactions on open networks. At the same time, gadgets that often connect to public open Wi-Fi networks are especially vulnerable to cyber threats.
Insecure connection. How to protect your data when using open Wi-Fi?
There are several fairly simple rules that will allow you to keep personal information confidential when using open Wi-Fi points in cafes, hotels, airports and other public places.
For example, you should not unconditionally trust those networks that you can immediately log into and start working on the Internet without any passwords. Such Wi-Fi connections are usually provided today in all shopping centers, clubs, cinemas and even transport.
Moreover, if you see that the network is asking for a password, you should also be vigilant. Fraudsters can find out the password to a network, for example, in a coffee shop, and then create a fake connection with the same password. This makes it easy to steal personal data of a person. In this case, you should trust only those network names and passwords that the employees of this establishment provide you with.
To be as safe as possible, you should turn off your Wi-Fi connection when you're not using it. This will also save battery power. Experts also advise disabling the function of automatically connecting to existing Wi-Fi connections.
If you are not 100% sure of the security of the wireless network you are using, but you still need to go online, try to do simple things, for example, checking email, reading social networks. But in such a situation, you should not make any transactions in an online bank or enter your confidential data anywhere (bank card number and especially CVV code).
Some social networks require manual security settings. In order not to worry about potential attacks from cyber fraudsters, just enable the “Always use a secure connection” (HTTPS) option in the settings. It is recommended to enable this function when visiting all services that you are not sure are properly protected.
If possible, you should use a connection via a virtual private network (VPN). This is an excellent option for data protection, the only thing is that it is not free. Traffic on such a network is routed through a secure tunnel in encrypted form.
You should definitely use specialized comprehensive anti-virus protection tools. They warn of potential danger if you connect to a questionable Wi-Fi network, and will not allow you to share passwords if there is a threat of leakage.
How to prepare your gadget for vacation?
To protect yourself as much as possible while on vacation, you should prepare your device for travel.
So, it is advisable to set a PIN code on all your devices. Blocking will save you from unauthorized access to your data, as well as simply from prying eyes.
In addition, it is advisable to install a program to track the location of the device and block it if the device is lost or stolen. For example, the Anti-Theft function in Kaspersky Internet Security for Android will allow you, if you have lost your phone, to remotely turn on the siren on it. You can also track the device's location on a map, lock it, and take a photo of the person who has it. As a last resort, you can even remotely clear the device's memory. This way, at least your photos and contacts won't fall into the wrong hands.
Also, train yourself in advance not to share sensitive data while connected to public Wi-Fi networks.
Be sure to update your device software before your trip and back up all your files. And set a pop-up blocker in your browser.
In addition, you should worry about the safety of other devices that you take with you and that can be synchronized with your mobile device. Install a comprehensive antivirus for smartphones and tablets on Android, as well as for laptops on Windows and Mac.
Latest site materials
Video

International postal tracking
To track your parcel you need to take a few simple steps. 1. Go to the main page 2. Enter the track code in the field with the heading "Track postal item" 3. Click on the "Track parcel" button located to the right of the field. 4
Windows 8

How to delete a page on VK?
Every person registered on a social network may want to delete their page completely, or for some period of time. The time given by developers for reflection varies from one month to six months. This is due
Browsers

Finding duplicate files using CCleaner How to find identical files on your computer
Good day. Statistics are an inexorable thing - many users sometimes have dozens of copies of the same file (for example, a picture or a music track) on their hard drives. Each of these copies, of course, takes up space on the hard drive. A
Browsers

A quick way to install Windows without a disk or flash drive
I first encountered the question of how to install Windows on a computer at checkout 4. There was no Internet where I lived, so this question was especially difficult for me. At the end of the 4th grade, my father bought me a book, I don’t remember exactly what it was called, approximately “Os
Programs
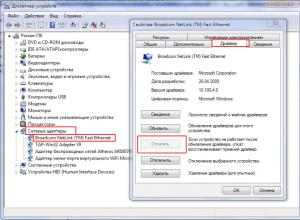
If the Internet does not work after reinstalling Windows... A few tips
Drivers for the network adapter are needed on any Windows device where you plan to access the Internet. This cannot be done without them. After installing Windows, you need to install all the necessary drivers. You also need to download it for the network adapter
Video
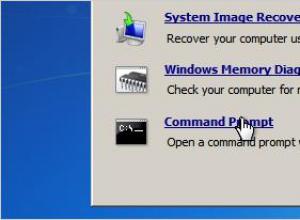
Windows 7 asks for password when logging in
All passwords, especially complex ones, are often forgotten by us. Sometimes it happens that we write down their meaning only on a piece of paper, which is soon simply lost. In general, the situation is typical. Beginners are sometimes frightened by the fact that if they have forgotten their password, they cannot log into the system.